Vulnerability Triage
Within Black Duck Binary Analysis, vulnerability triage refers to the ability to exclude specific known vulnerabilities of a third-party component from the analysis score of a scanned application.
Vulnerability triage can be useful in the following situations:
- You have patched a third-party component in a manner that either fixes or disables the known vulnerability.
- You have included a third-party component in such a way that the known vulnerability within it cannot be accessed or executed (that is, the attack vector cannot be exploited).
- The third-party component is included in but not used by the scanned application.
In such circumstances, you are aware of the presence of the vulnerability, but you have also taken the steps necessary to neutralize it. On that basis, you might wish to suppress these specific findings from your analysis reporting, thereby reducing noise. Triage provides you with a means of having this control.
Important: Keep in mind that excluding known vulnerabilities through triage does not in and of itself remove the risk of exploit from your application. Furthermore, Black Duck Binary Analysis only detects the presence of components with known vulnerabilities within your application; it does not detect whether the vulnerabilities in those components can be exploited or not.
Triaging Known Vulnerabilities in Components
When viewing a scanned application, you can triage the known vulnerabilities within third-party components. This excludes them from the analysis score.
Note that Triage Mode must be enabled by an administrator.
- In the Components list, select a component that contains BDSAs or CVEs that you wish to triage. If the component has both, both will be triaged.
- In the component's Vulnerabilities list, select one or more BDSAs or CVEs to
be triaged.
Figure 1. Select components. 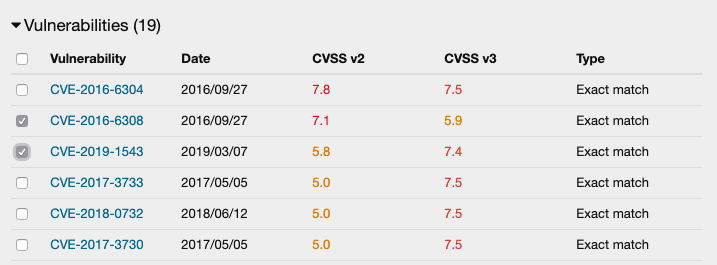
You can triage more than one vulnerability at a time (batch processing). Keep in mind that the same rationale and scope will apply to all vulnerabilities within the batch. If the vulnerability has both BDSAs and CVEs, both will be triaged at the same time.
- Under Triage, select Triage selected vulnerabilities.
Figure 2. Select Triage selected vulnerabilities. 
- In the Triage vulnerabilities dialog, select values for
Rationale and Scope. Optionally, you may enter text in the
Description field.
The values that you enter will apply to all of the BDSAs or CVEs that you have selected. If you wish to cancel the operation, then select Close.
- To apply the values, select Save.
Component vulnerabilities that have been triaged are displayed in the component's Triaged vulnerabilities list.
Triage Rationale
You can indicate a rationale for excluding a known vulnerability. When triaging known vulnerabilities, you can select from among the following options:
- Vendor patched: The third-party component has been patched by the vendor, thus negating the known vulnerability
- Feature disabled: The third-party component is configured in such a way that the known vulnerability is inaccessible from within the scanned application
- Other: You can enter text describing the rationale
- Comment (needs review): The vulnerability is known and needs to be addressed.
Triage Scope
You can apply a scope to a triaged vulnerability within a third-party component and you can choose to apply it on an application, group, or account level.
When triaging known vulnerabilities, you can select from among the options below. Note that the corresponding API values are provided within parentheses.
- Account (CA): Applies to all uses of the component within the company account
- Group (G): Applies to all uses of the component within the group
- Application (R): Applies to uses of the component within the same scan only
- Application name (global scope) (FN): Applies to uses of the component within scanned applications having the same file name
- File hash (global scope) (FH): Applies to uses of the component within scanned applications having the same file hash
Reverting Triaged Vulnerabilities
When viewing a scanned application, you can revert the status of triaged vulnerabilities within third-party components. After reverting, the vulnerability will be included in the scanned application's analysis score.
Note that Triage Mode must be enabled by an administrator.
To revert one or more triaged vulnerabilities:
- In the Identified 3rd party components list, select the package that contains the BDSAs or CVEs that you want to triage.
- Under Triaged vulnerabilities, select the BDSAs or CVEs that you wish to
revert. You can select one or more BDSAs or CVEs at a time.
Figure 3. Select triaged vulnerabilities. 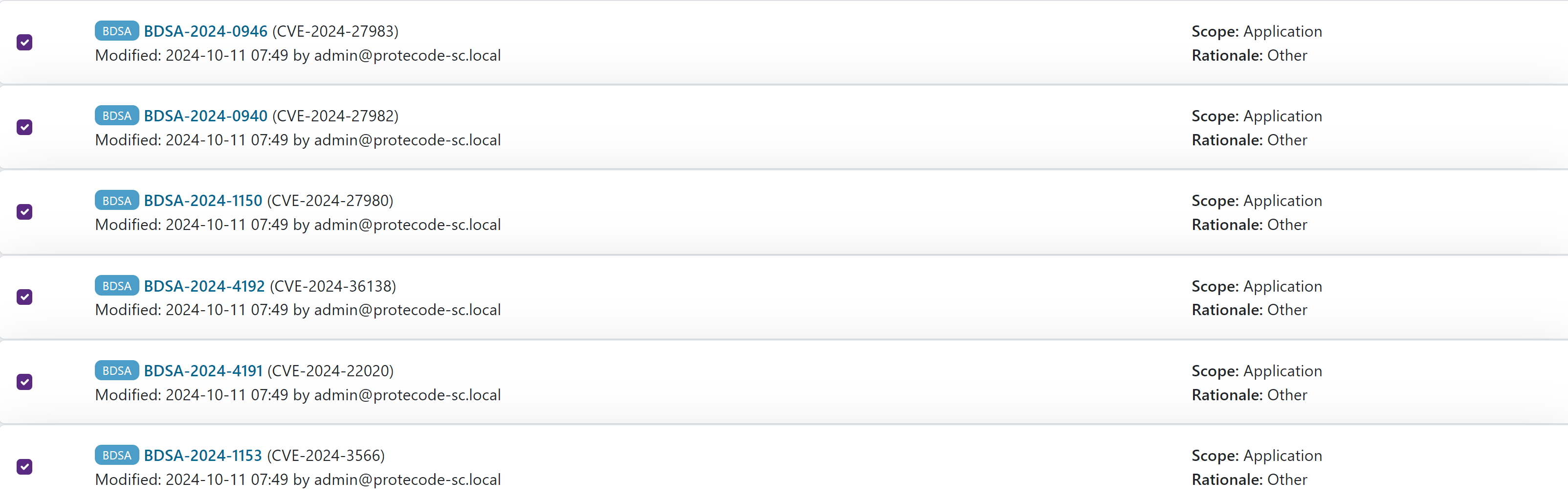
- Select Remove selected triages.
Figure 4. Remove selected triages. 
- In the Remove triages dialog, select Remove to complete the
operation.
If you wish to cancel the operation, then select Close.
The reverted vulnerabilities will be returned to the component's vulnerabilities list.
