Overview
Black Duck Binary Analysis is a software composition analysis (SCA) scanner for compiled code.
Problems Solved
Here's what it can do for you:
- Provides a clear view of risk. Black Duck Binary Analysis gives unmatched visibility into open source and third-party code in applications and containers. Black Duck Binary Analysis gives you the information you need to verify that your product has exactly the components you expect, that those components are up to date, and that no inappropriate software licenses have been used. It creates a high-level overview of the composition and overall health of software, including desktop and mobile applications, embedded system firmware, and more. Better visibility leads to better decisions regarding mergers and acquisitions, as well.
- Helps to manage the risk. Black Duck Binary Analysis provides a comprehensive solution for managing security, quality, and license compliance risk.
- Informs your decisions about software consumption. Reduce security risks and the threat of license noncompliance. Identify known open source vulnerabilities, licensing obligations, sources of sensitive data leakage, and application permission requirements. When you're acquiring a product, Black Duck Binary Analysis allows informed decisions, minimizes your risk, and maximizes the value of the product.
- Maintains security as threats evolve. The receipt of a detailed Bill of Materials for every analyzed product keeps your supply chain secure. Black Duck Binary Analysis automatically updates you when a new vulnerability applies to previously scanned software. This information allows you to make decisions, mitigate or eliminate risks, or negotiate with suppliers.
Use Cases Addressed
- Procurement: If you are acquiring a product, Black Duck Binary Analysis provides visibility into the risk profile of the product, allowing you to make informed decisions and negotiate with your vendor to minimize your risk and maximize the value of the product.
- Mergers and Acquisitions: Black Duck Binary Analysis makes it easy to analyze existing products to understand their composition and associated risk. Better visibility leads to better decisions about product integration and security risks.
- Supply chain security: Any organization looking to minimize risk in its supply chain can put Black Duck Binary Analysis's results to good use. For each analyzed product, Black Duck Binary Analysis provides a BOM, an accurate view of vulnerabilities and risk. This information allows you to make decisions, mitigate or eliminate risks, or negotiate with suppliers.
- Development: For builder organizations, Black Duck Binary Analysis provides automation for tracking third-party software components. As a critical check on the products you are building, Black Duck Binary Analysis gives you the information you need to verify that your product has exactly the components you expect, that those components are up to date, and that no inappropriate software licenses have been used.
Why and How
Using third-party code saves time and money, but exposes your project to risks, in terms of security, code quality, and licensing. Black Duck Binary Analysis addresses that risk when you don't have access to source code. It analyzes software binaries, compiled applications, or docker images. It can scan virtually any compiled software, including desktop and mobile applications, embedded system firmware, and more. (It does not analyze source code; however, standard Black Duck can do that.)
Black Duck Binary Analysis recognizes thousands of existing libraries and open-source projects, as well as their components. If it does not recognize components because it is a proprietary or commercial component or it’s possibly a missing OSS component in the Knowledgebase, you can teach the components using the Vendor Components functionality in Black Duck Binary Analysis, and they will be recognized thereafter. (See the User Guide for more information.) You may also request adding an OSS component to the Knowledgebase by opening up a Support request.
Black Duck Binary Analysis's composition analysis helps you determine whether any of your software components are vulnerable to bugs such as Heartbleed (CVE-2014-0160), particularly in cases where you either cannot run dynamic tests against your systems or are afraid that active vulnerability scanning might have adverse consequences.
Basic Usage
When you scan your code with Black Duck Binary Analysis, it analyzes your binary files and compares the results with those stored in a common database. Components can be recognized by a number of matching methods, including the use of metadata extracted from binary files or .jar files; package manager data, manifest files, or a checksum of a .jar file. (In the user interface, you can find the matching method that was applied to any file in its component description.)
To begin scanning your binaries, see Scanning Your Apps.
When you teach Black Duck Binary Analysis to recognize your components, you can track and manage the vulnerabilities that are found in them. These remain in your organization and are never shared in the common database (In fact, customers cannot add components or information to the common database – so your proprietary files cannot be mistakenly exposed).
To teach Black Duck Binary Analysis your components and vulnerabilities, see Managing Components and Vulnerabilities.
After scanning your application (including third-party and proprietary code), Black Duck Binary Analysis produces a bill of materials (BOM): a comprehensive listing of the components, their known vulnerabilities, and the associated software licenses.
A comprehensive dashboard helps you manage vulnerabilities, leaks of potentially sensitive information, and licensing issues, discovered by Black Duck Binary Analysis. Additionally, you can download scanned binary files and add custom data to scan results.
You can decide to exclude known vulnerabilities and information leaks. For more information, see Triaging Vulnerabilities and Information Leaks.
Features
BDBA supports different workflows for binaries, SBOMs and containers.
Binary Artifact Scanning
For scanning your software artifacts you can upload or fetch any file and view the scan results. For more information, see Scanning Your Apps.
SBOM Workflows
BDBA supports various workflows regarding Software Bill-of-Materials (SBOM) standard documents.
Import
With BDBA it is possible to import SBOM documents created by any SBOM tool in the following formats:
- CycloneDX: JSON, XML up to spec version 1.6 - https://cyclonedx.org/specification/overview/
- SPDX: JSON, XML, YAML, RDF+XML, TAG+VALUE up to spec version 2.3 - https://spdx.dev/use/specifications/
Currently, all SBOM components and their filepaths will be imported along with metadata for the SBOM. Additionally, any component annotations present in the SBOM document like PURL, CPE, creator information and comments will be shown in the results. To import a SBOM document, just proceed with the normal way of scanning files, that is, use the upload or fetch feature.
Any SBOM document will be recognized automatically even if part of an archive. Multiple SBOM documents will be imported into the same scan results and shown on the BOM. For more information, see the Vulnerability analysis tab.
It is possible to group BOM results by the SBOM document they are imported from. Additionally, one can view more details on each SBOM document found in the scan and also download each document separately from a scan on the Details tab.
Export
Any scan results can be exported to an SBOM with the following formats:
- CycloneDX: JSON, XML spec versions 1.6
- SPDX: JSON spec versions 2.2 and 2.3
The user can add annotations to the components in the BOM before exporting to enhance the created SBOM document. For more information on this, see SBOM fields. If a scan result BOM is the combination of multiple imported SBOMs and binary artefacts scan, then all the results will be combined into one single SBOM on exporting.
Containers
BDBA allows you to scan Docker and OCI containers from files that are created from container images and uploaded to BDBA for scanning. Additionally, BDBA can fetch container images by name and label via the fetch function from container registries. In general, any containers image will be recognized from a scan and the number of found containers will be shown in the results. When choosing the dedicated container view in the results, BDBA will show metadata for each container.
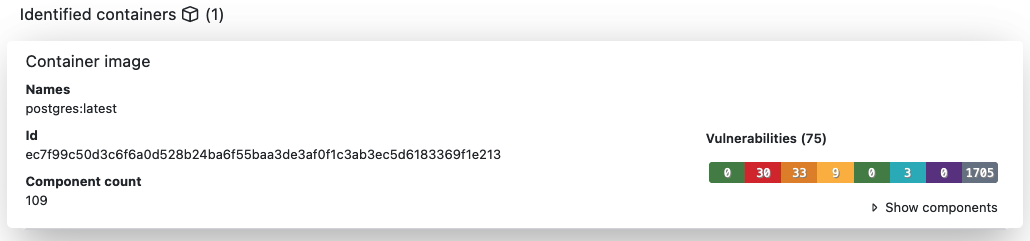
In this view it is possible to group components found in a container and show them for each separate layer or apply squashing to combine layers of the whole container into one single layer.
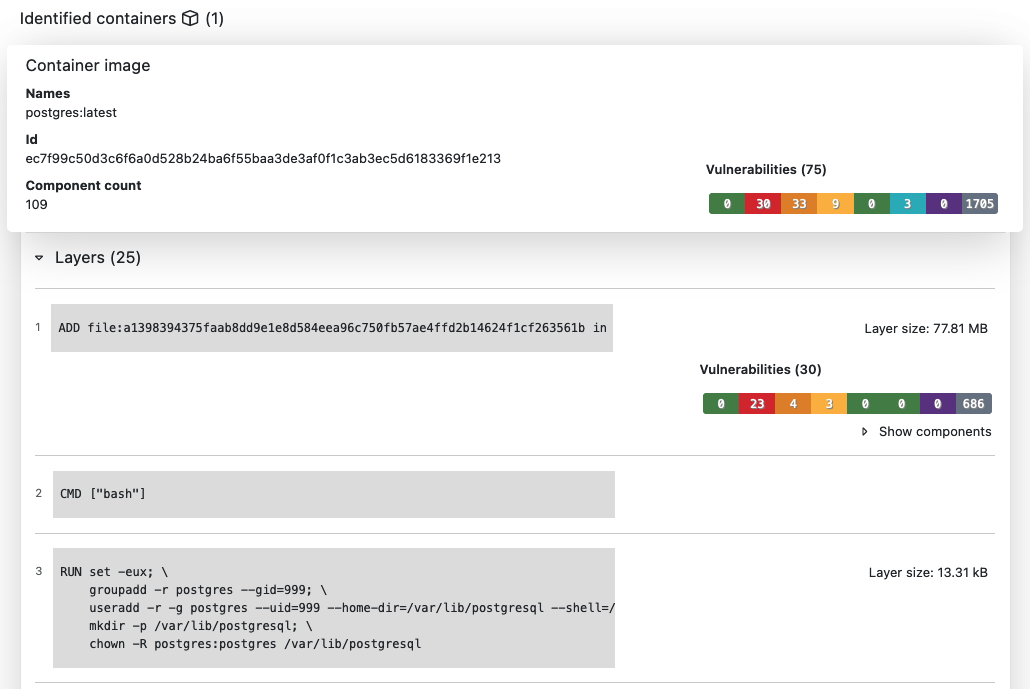
The squashing will also take removed files or container whiteouts in layers into account when computing the final component results. In the layer view BDBA also displays the Dockerfile commands that were used to create that particular layer.
Advanced Features
Black Duck Binary Analysis contains the following advanced features:
- Black Duck Binary Analysis comes with a powerful JSON API that allows you to upload software and retrieve results.
- Black Duck Binary Analysis is mobile compatible and can be used from mobile phones and tablets.
- Black Duck Binary Analysis allows you to generate various reports from high-level dashboards to detailed trending reports between different versions of the software package. Reports can be created from the Export menu on the group page.
- Black Duck Binary Analysis has an audit trail feature which logs timestamp,
user, group, action type, verb and related objects for the following events:
- Log in and log out
- Add, edit and remove group
- Add, edit and remove user
- Upload, analyze, edit and remove applications
- Change settings
- Export audit trail CSV
Analysis Configuration File
The analysis configuration file allows you to pass data and configuration options to the scanner while scanning an application. At the moment it supports adjusting component versions, detected distros and distro versions, triaging vulnerabilities and adding new components.
The analysis configuration file is in .yaml format.
To use the the analysis configuration file, follow these steps:
- Name the analysis configuration file .bdba.yaml or .bdba.yml.
- Place it in the archive with the binary to be scanned.
- Scan the binary.
- The uploaded file is visible in Details > Analysis Configuration File.
- After an application has been scanned with the analysis configuration file,
the
config-filetag is displayed next to the vulnerability which has been overridden in Vulnerability Analysis > Components > Historical vulnerabilities. - It is also possible to use a remote analysis configuration file via URL in the scan. This option will ignore any uploaded analysis configuration file.
- The remote analysis configuration file can be set at product or group level. For group level instructions, see Group Scan Options.
For more information about the Analysis Configuration File, see the Appendix.
New Vulnerabilities Found After Scanning
You can enable automated alerts in case a new vulnerability is reported against a component that is included in previously uploaded software packages. With this feature, as soon as Black Duck Binary Analysis becomes aware of a new vulnerability affecting a particular third-party component, you will get an immediate email notification with details about the vulnerability and the software packages that are affected.
This feature is extremely useful for managing your open source and third-party code inventory, and for staying on top of what new vulnerabilities may affect your code base through use of third-party components.
